Overview
ReportWORQ can integrate with select Microsoft 365 resources including SharePoint, Teams, Email, and Entra Authentication. To set up authentication between ReportWORQ and Microsoft 365, you register an Azure app and then authenticate to it using credentials recorded during registration.
Note: By default, the Microsoft account you use to authenticate to Microsoft 365 will also be used by the ReportWORQ Email Distributor, if configured and enabled. We recommend you create a dedicated Microsoft user account for ReportWORQ purposes.
This article includes the following sections:
Azure App Registration
To use Microsoft 365 Authentication with ReportWORQ you must first register an application in Microsoft Azure.
To register an Azure application:
Log on to the ReportWORQ server using an account that has Microsoft Azure Administrator privileges.
Log into your Azure tenant and create a new App Registration.
Provide a name for the application and select the appropriate API access.
Most users choose Accounts in this organizational directory only.
Do not provide a Redirect URI in this step.
Record the Application (Client) ID, and Directory (tenant) ID from the Overview area.
Select Manage > Certificates & secrets from the left pane.
Create a New client secret with a description and expiry date.
Set a reminder to create a new secret and update ReportWORQ before it expires.
Important: Record the Secret value (not the Secret ID) for use in the ReportWORQ configuration.
Select Manage > Authentication from the left pane.
Select Add a Platform and select Web.
Note: Selecting any platform other than Web will not work properly..png)
Select the option to enable Access Tokens.
Enter the following redirect URI, and then select Configure.
http://localhost:8300/signin-oidc
For each of the following redirect URIs, in the Web area, select Add URI and then enter the URI:
http://localhost:8300/server/v0/get-office365-smtp-token
http://localhost:8300/server/v0/get-office365-sharepoint-token
Select Save.
Redirect URLs
Azure App Registrations limit non-SSL HTTP redirect URLs to localhost. If ReportWORQ is running under HTTPS then you can adjust the server name and port to allow Microsoft 365 Authentication to be performed from a user workstation. Otherwise use localhost, as shown above, and the one-time authentication must be performed from a browser on the machine that ReportWORQ is installed on. The ReportWORQ Administrator will need to remote into the server to perform the authentication so that the redirect URL localhost is valid.
Microsoft 365 Authentication
This section describes how to authenticate to Microsoft 365, using credentials you recorded during Azure app registration.
After authentication is established, you can limit authorization scopes (optional).
To authenticate ReportWORQ to Microsoft 365:
Log in to a ReportWORQ Administrator account.
From the Administration menu, select Microsoft 365.
In the Provider Settings area, enter the credentials you recorded during Azure app registration (Tenant Id, Client Id and Secret value).
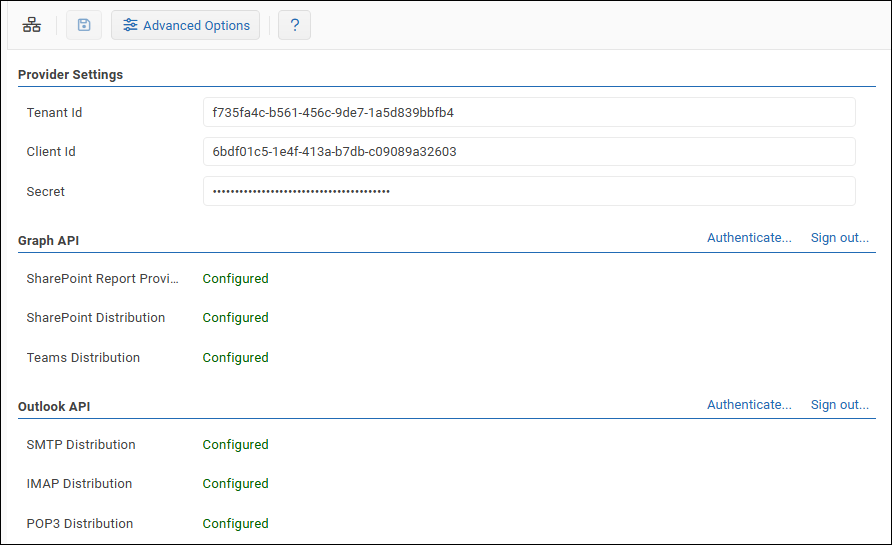
Save changes.
In the Graph API area, select Authenticate, and then authenticate to Microsoft 365.
If prompted to consent to requested permissions, select Consent on behalf of your organization, and then select Accept.In the Outlook API area, select Authenticate, and then authenticate to Microsoft 365.
Common Authentication Errors
Did you see this message?
AADSTS50011: The redirect URI 'http://servername:8300' specified in the request does not match the redirect URIs configured for the application
This error message appears when the user attempts to authenticate and the browser URL doesn't match the redirect URL that the Azure IT Administrator entered into the Azure App Registration. The default non-SSL configuration requires that the browser address appear as http://localhost:8300. If your browser URL appears differently then you may need to remote into the server where ReportWORQ is installed and then perform this authentication step from a browser on that machine using http://localhost:8300.
Limiting Authorization Scopes
By default, ReportWORQ requests all authorization permissions (scopes) required to support its full range of integrations with Microsoft 365 applications. For example, ReportWORQ can be configured to deliver reports via Microsoft Teams or to folders on SharePoint. Your organization may or may not require use of all such integrations.
Some organizational IT policies require access to be strictly limited to required authorizations only. You can view the list of scopes requested by ReportWORQ and limit the list as required.
Graph Scopes to support ReportWORQ are as follows:
Required for ReportWORQ (mandatory):
openid — allows single sign-on (SSO) authentication.
offline_access — allows ReportWORQ to refresh user sign-ons automatically.
https://graph.microsoft.com/User.Read — allows ReportWORQ to access user profile information.
https://graph.microsoft.com/User.ReadBasic.All — allows ReportWORQ to access user profile information.
Required for ReportWORQ to use Microsoft Teams:
https://graph.microsoft.com/Team.ReadBasic.All
https://graph.microsoft.com/Channel.ReadBasic.All
https://graph.microsoft.com/ChannelMessage.Send
https://graph.microsoft.com/Chat.Create
https://graph.microsoft.com/Chat.ReadWrite
https://graph.microsoft.com/Files.ReadWrite.All
Required for ReportWORQ to use Microsoft SharePoint:
https://graph.microsoft.com/Sites.Read.All
https://graph.microsoft.com/Sites.ReadWrite.All
https://graph.microsoft.com/Files.ReadWrite.All
Required for ReportWORQ to use Graph Email for report distribution:
https://graph.microsoft.com/Mail.Send
https://graph.microsoft.com/Mail.Send.Shared
https://graph.microsoft.com/Mail.Read
https://graph.microsoft.com/Mail.ReadWrite
Microsoft 365 scopes required for using legacy Outlook functionality (POP, IMAP, and SMTP Email) are as follows:
openid
offline_access
https://outlook.office.com/IMAP.AccessAsUser.All
https://outlook.office.com/POP.AccessAsUser.All
https://outlook.office.com/SMTP.Send
To limit authorization scopes:
In Administration > Microsoft 365, select the Advanced Options button.
.png)
The Advanced Options pane appears, listing authorization scopes in two groups, Graph API and Microsoft 365.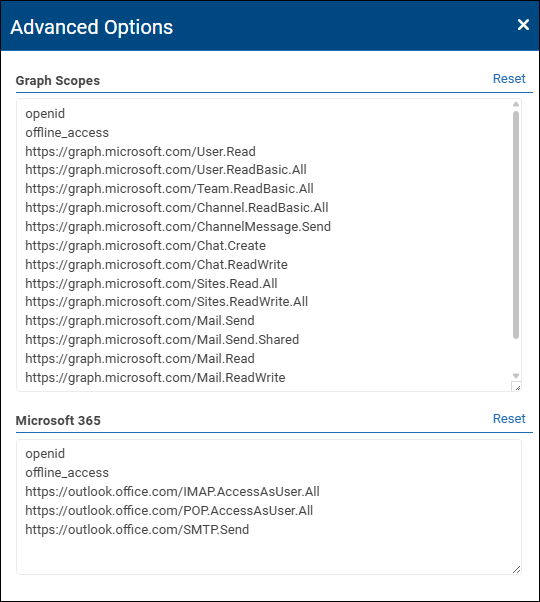
In the list of scopes, delete the ones you do not want enabled. Note which scopes you removed.
Tip: To restore the list to the default (all scopes), select Reset.Close the Advanced Options pane.
For each group of scopes you edited (Graph API and/or Outlook API), do the following:
Select Sign out.
Select Authenticate, and then sign in.
In Azure App Registration, navigate to Manage > API permissions, and do one of the following for each of the scopes you removed:
If you want to allow ReportWORQ Administrators to add the scope again in the future, select Remove permission.
If you want to prevent ReportWORQ from adding the scope again in the future, select Revoke admin consent.
Microsoft 365 Services
This step should be performed by the ReportWORQ Administrator
With the Azure App Registration created and the ReportWORQ Microsoft 365 configuration applied and authenticated, you can now begin to leverage Microsoft 365 for the following services:
Authentication
Report Providers
Distributors
Data Collection